Cloud Confusing
Explaining hosting, AWS, Wordpress, static sites, and all manner of cloud solutions.
How to Use Multi-Factor Authentication to Improve AWS Security (And What Amazon Needs to Improve)

The centralization provided by AWS is great — all your web services are in one place with one bill. But if your account is compromised (and you don’t have proper permissioning / IAM) things can go very bad very quickly. So you’re going to want to lock down access to accounts as thoroughly as possible, which means multi-factor authentication of user logins.
And yes, that’s mutli-factor (MFA), not two-factor. Two-factor authentication (TFA or 2FA) is great, but when additional security levels are possible and they can be done almost seamlessly, they make total sense. With the loss of SMS authentication at the end on January 2019 it’s debatable whether Amazon will have multi-factor (as in more than two) or two-factor authentication but we’ll avoid the semantics from this point forward and use the term that seems best in a given scenario.
AWS and MFA
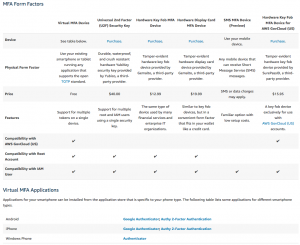
AWS’ multi-factory authentication home is here. It outlines much of what you’ll want to know. You can see it all in the chart placed at the bottom of this article (it’s big). If you don’t need any explanation hop on down to it for some quick answers to your security questions.
We’ll run quickly through the options and then talk about how to setup your multi-factor auth.
Important Note: Keep in mind that MFA is supported by the AWS console, but not by the CLI or API. This might be obvious given the limitations of those interfaces, but it’s worth mentioning since those are important ways people interact with their AWS account!
YubiKey and U2F on AWS
On September 26, 2018 Amazon announced YubiKey support for AWS. This was a long-awaited announcement, as multiple companies (most notably Google) have come to recognized the effectiveness of what’s known as U2F (Universal 2nd Factor) authentication. Hardware security devices like the YubiKey are useful for multiple devices, don’t require an app, have native support in all popular browsers, and now have an excellent track record of security success. YubiKeys can be used for multiple accounts where in a one-time password (OPT) in an auth app you need to have a new entry for each login.
Amazon links their MFA page to this specific Yubico security key (affiliate link) which sells for $40. The page also links to this OTP fob (effective but annoying) and this OTP card, but YubiKey seems to the preferred route moving forward. Other hardware devices (Trezor, self-signed attestation, etc.) are not yet supported for MFA usage.
One major downside of a YubiKey or other form of hardware-based security is loss. AWS does not support multiple U2F signatures per user. So if you lose your keys or leave them at home, you might not be able to (easily) get into your account. It’s for this reason (mainly loss) that some service will allow a user to register more than one key. Plus it’s just handy: keep one key on you and the other in your home safe, or keep at work and one at home in your desktop USB port if you are comfortable with the physical security of both places. These practices aren’t strictly ideal for security, but they are practical for many people. Enough people do this by getting a YubiKey Nano and just never removing it from their laptop.
(Yes, since you presumably own the IAM you could create a backup account and have your backup u2F key associated with that, but that’s not only annoying it’s going to be quite confusing to keep track of.)
2FA Apps
Amazon Web Services support a small number of authentication apps (what Amazon calls “Virtual MFA Applications”). These are ones you have likely used before:
- Android and iOS: Google Authenticator, Authy
- Windows Phone: Authenticator by Microsoft
These apps can be annoying if you lose, break, or upgrade your phone, but they are generally very good security. They offer a form of de facto multi-factor auth since your phone presumably has some sort of security mechanism on it (face scan, fingerprint reader, etc.), plus getting someone’s phone away from the is a non-trivial task.
SMS Authentication
Amazon currently supposed SMS (text) based authentication but is in the process of phasing it out. SMS auth has seen a number of issues in the past, through SMS hijacking and exploiting known security flaws in cellular security. Current SMS auth users will have the feature until February 2019, but then it will be phased out. It’s not possible to add this feature if you don’t already have it enabled.
Currently SMS authentication can be cookied with a “Trust This Browser” setting so while it’s not someone you’d want to rely on by itself in 2018, it’s a useful and seamless layer. Amazon hasn’t said explicitly why SMS security is being phased out, but we know it’s not worth using by itself, so that might be reason enough.
How to Enable Multi-Factor Authentication on AWS
Role-based security in AWS is handled through the IAM panel (Identity and Access Management). This is where you set your security policy (password length etc.) and create/edit user roles. To setup TFA/MFA/UFA you needs to go to the Users page and then to the Security Credentials tab.
Then go to “Assigned MFA device” and click “Manage.” Now you can choose between a Virtal MFA (authentication app), a YubiKey (if your browser supports it), or another hardware security device. Pick your device and follow the steps, in under a minute your new form of security should be ready to go.
Important Note: Amazon will support one MFA per user so you can’t configure a YubiKey and then go ahead and add on Authy. It’s one or the other for now. This means they can’t be layered (as in both required) nor can the be used interchangeably (as in, only one of the two is required).
AWS MFA Chart
Sal September 26th, 2018
Posted In: AWS
Tags: Authentication, IAM, Universal 2nd Factor